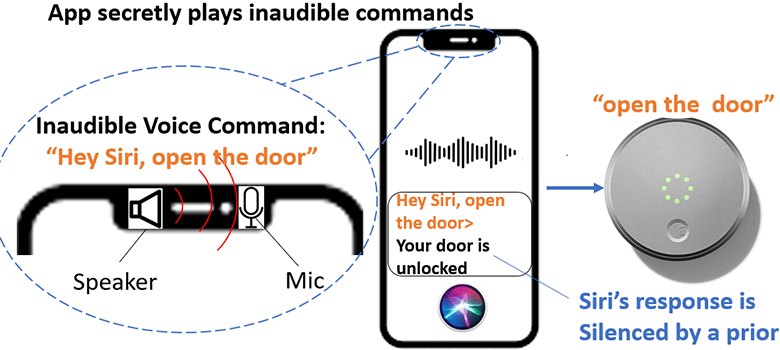
Uncovering the unheard: Researchers reveal inaudible remote cyber-attacks on voice assistant devices | UTSA Today | UTSA | The University of Texas at San Antonio

Zero-Click' hacks are growing in popularity. There's practically no way to stop them | Technology News,The Indian Express

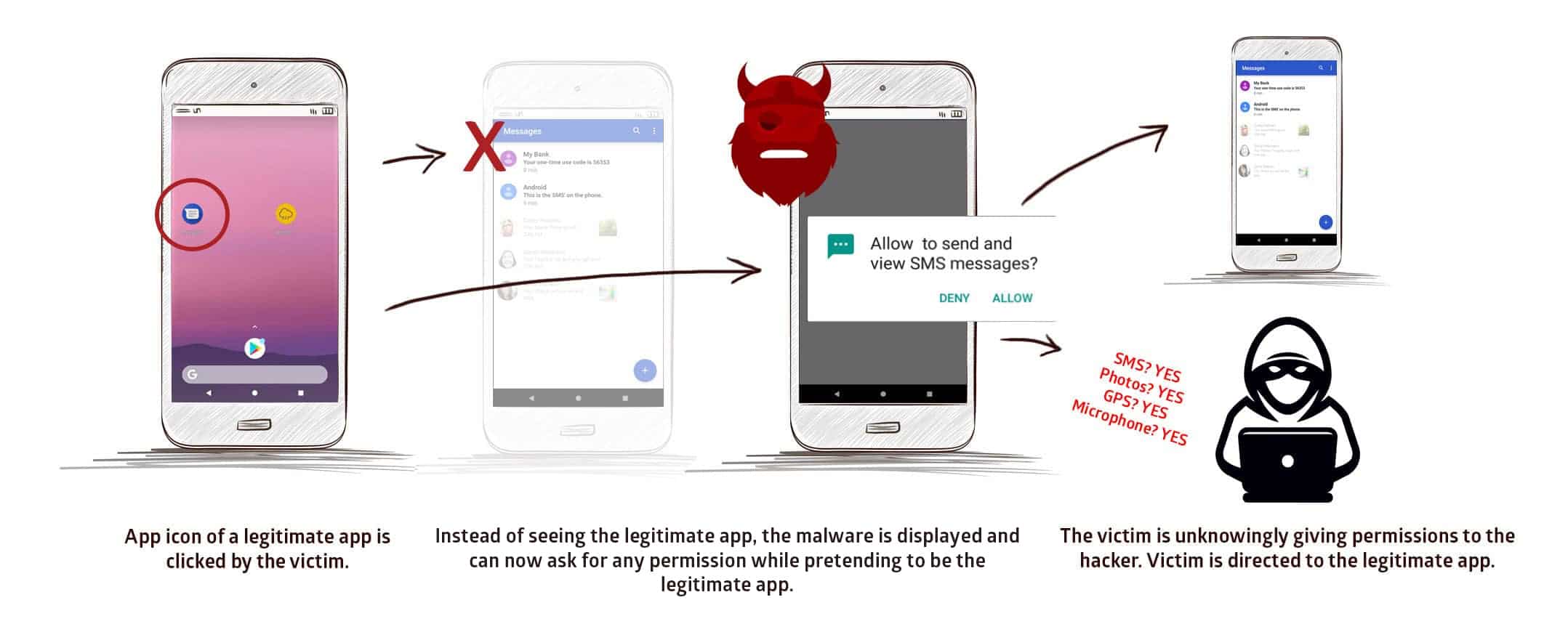
Sync NI - Android phone vulnerability gives apps access to your camera and microphone without permission